Rayven security features are robust, but without compromising usability.
With valuable data and insights being communicated from the cloud to the Edge, success depends on ensuring data integrity, confidentiality + mitigating cyber security risks - something the Rayven Platform has at its very core.
Security without usability would be useless, so we’ve been careful not to encumber end users, too. By leveraging data encryption and our own proprietary technologies, we guarantee a brilliant user experience and have made our platform the safest, most secure in the world.

Rayven security features include:
API Authentication (username + multifactor tokens)
Device authentication using device keys with 256-bit SSL encryption
User data encryption at rest with triple DES + password encryption (SHA256 hash)
User access revalidation via API + dynamic updates via API (push or pull)
Device security health checks via automated polling and / or pull request
Solutions can be hosted in Rayven's secure private cloud (optional)
Data encryption of data when in-transit, at-rest or during use (all 256-bit)
Custom security event monitoring and incident handling at user + device levels
Optional single sign-on (SSO) available as-standard
Forced password requirements, including characters, numbers + more
Rayven Defender monitors data flow to devices to identify anomalies,
tampering or error
Disaster Recovery as-standard to ensure data is not corrupted or lost (Rayven Private Cloud-only)
Custom security that's ready for industry, real-time data + AI:
get technology that's fit-for-purpose.

High-availability security architecture.
The Rayven Platform is designed to always provide a high-level of operational performance and uptime with no single point of failure. This achieved using the following:
- All web servers + databases are mirrored across multiple virtual machines
- All databases + services are redundant
- Data is replicated across geographical zones
- Our system architecture allows us to add/change nodes, storage + services without downtime, so we can easily scale-up resources with no interruption to services
- Our systems run on Microsoft Azure infrastructure, which is a highly-resilient, enterprise-grade environment
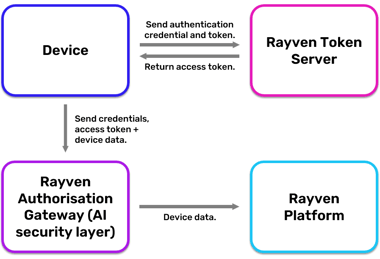
Rayven's basic device authentication model.
Rayven boasts an array security technologies that give fail-safe's fail-safes.
- TLS Handshake Protocol: Client and server authenticates with each other and selects an encryption algorithm prior to sending data.
- TLS Record Protocol: Works on top of the standard TCP protocol to ensure that created connections are secure and reliable. It also provides data encapsulation and data encryption services.
- SSL: For encrypting data sent between user operated devices and the platform.
- Certificate-based device authentication: Private and public key pair allows additional authentication at the physical layer. The private key is stored securely in the device and is not discoverable outside the device.
- Security (bearer) tokens: To authenticate devices and services to avoid sending keys over the network.
- Device authentication: Enables the client and server to authenticate each other by device ID.
- Database encryption: (Private cloud only), encrypt structured database content at-rest.
- SFTP: Establish a secure connection to transfer files and traverse the file system on both local and remote systems.
- Username + password: Client and server authentication via username and password.
- VPN: Security at the whole-of-server level for devices and/or users to connect to the platform (only available for private cloud customers).
Rayven Platform Security FAQs:
A defence-in-depth approach covering identity, data, network, runtime, and operations—backed by auditability and governance.
TLS 1.2+ for all transport; AES-256 (or deployment-equivalent) encryption at rest, including backups/snapshots.
Yes - OAuth2/OIDC, SAML, enterprise IdPs (e.g., Azure AD/Entra), MFA, SCIM provisioning (where configured).
Fine-grained RBAC with workspace/environment isolation, row/field-level controls, secrets management, and policies.
Comprehensive audit logs for user actions, data changes, and workflow executions; logs/metrics/traces with alerting.
Network segmentation, private networking options, IP allow/deny lists, rate limits/quotas, signed webhooks, and HMAC/JWT.
Regular scanning and patch cadence; dependency monitoring; CVE triage; emergency patch process for critical issues.
Configurable data residency and retention; deployment-specific controls to help meet regulatory requirements.
Yes, logical isolation by tenant/workspace; optional dedicated infrastructure in private cloud/on-prem/Edge.
Documented IR runbooks, severity-based SLAs, root-cause analysis, and customer communications for material incidents.























