Platform Security
Enterprise security at all points, as-standard.
Our platform features end-to-end encryption, user management + a host of vendor and proprietary security measures that keep your data secure at all points - plus get disaster recovery (DR) in-built.
Rayven delivers security without compromising usability.
With valuable data and insights being communicated from the cloud to the Edge, delivering successful outcomes depends on ensuring data integrity, confidentiality and mitigating cyber security risks - something our integrated data, AI + IoT platform and applications built on it has at its very core.
Security without usability would be useless, so we’ve been careful not to encumber end users, too. By leveraging data encryption and our own proprietary technologies, we guarantee a brilliant user experience and have made our platform the safest, most secure in the world.
API Authentication (username + multifactor tokens)
Device authentication using device keys with 256-bit SSL encryption
User data encryption at rest with triple DES + password encryption (SHA256 hash)
User access revalidation via API + dynamic updates via API (push or pull)
Device security health checks via automated polling
and/or pull request
Solutions can be hosted in Rayven's secure private cloud (optional)
Data encryption of data when in-transit, at-rest or during use (all 256-bit)
Custom security event monitoring and incident handling at user +
device levels
Optional single sign-on (SSO) available as-standard
Forced password requirements, including characters, numbers + more
Rayven Defender monitors data flow to devices to identify anomalies,
tampering or error
Disaster Recovery as-standard to ensure data is not corrupted or lost (Rayven Private Cloud-only)
Security is central to everything we do, making our platform the most secure + reliable in the world.
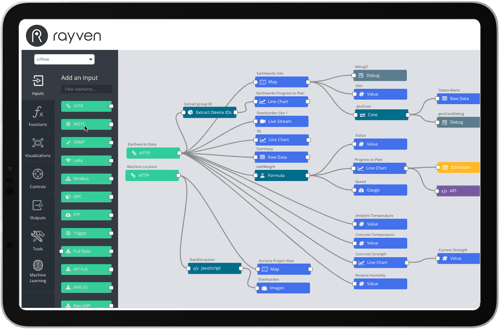
Custom-designed security for real-time data, IoT + AI: get technology that's fit-for-purpose.
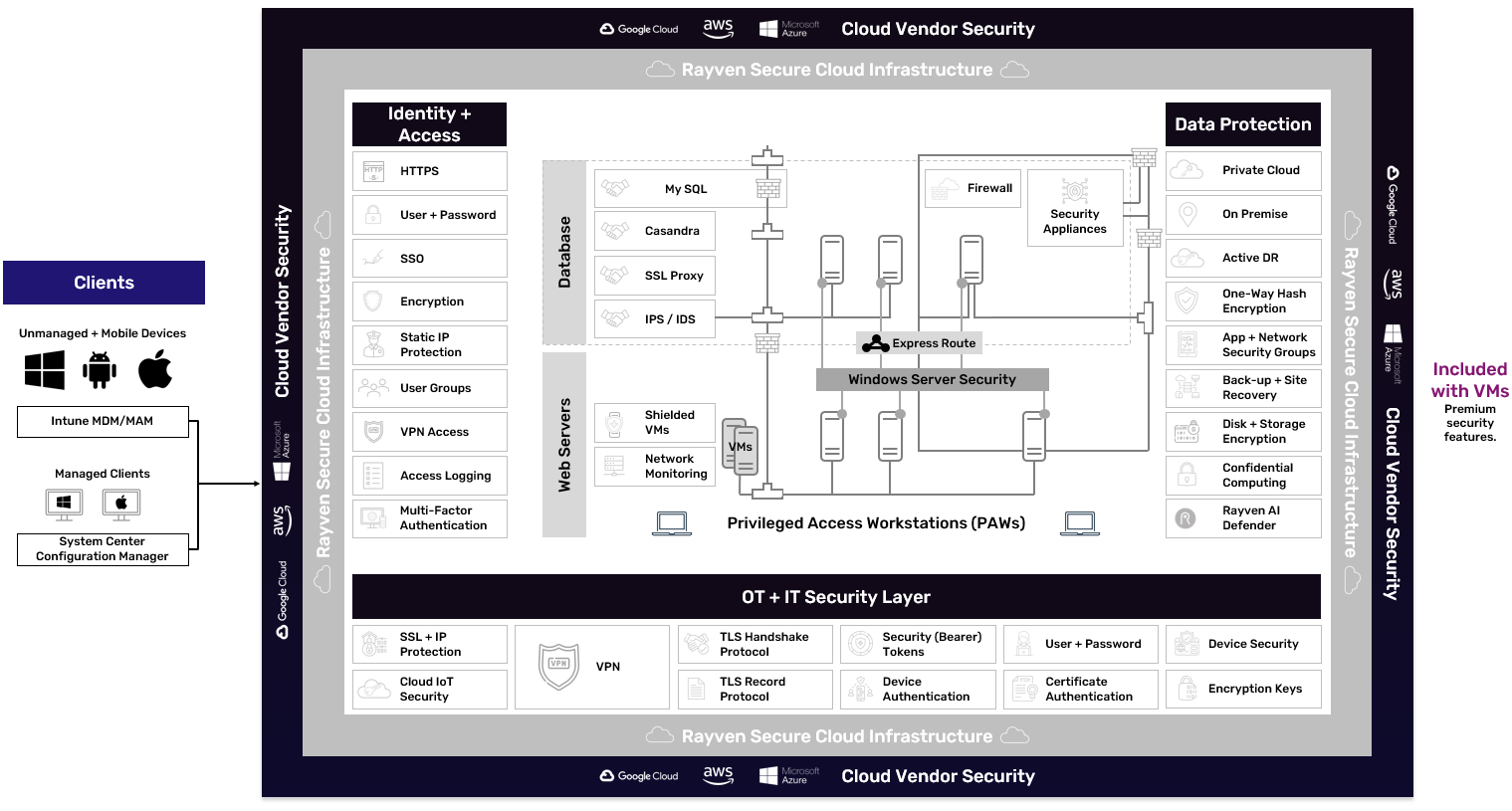
High-availability architecture.
Rayven is designed to always provide a high-level of operational performance and uptime with no single point of failure. This achieved using the following:
- All web servers + databases are mirrored across multiple virtual machines.
- All databases + services are redundant.
- Data is replicated across geographical zones.
- Our system architecture allows us to add/change nodes, storage + services without downtime, so we can easily scale-up resources with no interruption to services.
- Our systems run on Microsoft Azure infrastructure, which is a highly-resilient, enterprise-grade environment.
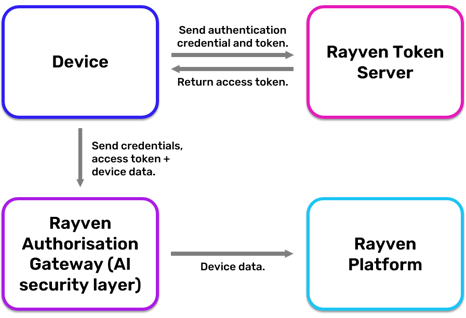
Rayven's basic device authentication model.
Rayven boasts an array security technologies to give fail-safe's fail-safes.
- TLS Handshake Protocol: Client and server authenticates with each other and selects an encryption algorithm prior to sending data.
- TLS Record Protocol: Works on top of the standard TCP protocol to ensure that created connections are secure and reliable. It also provides data encapsulation and data encryption services.
- SSL: For encrypting data sent between user operated devices and the platform.
- Certificate-based device authentication: Private and public key pair allows additional authentication at the physical layer. The private key is stored securely in the device and is not discoverable outside the device.
- Security (bearer) tokens: To authenticate devices and services to avoid sending keys over the network.
- Device authentication: Enables the client and server to authenticate each other by device ID.
- Database encryption: (Private cloud only), encrypt structured database content at-rest.
- SFTP: Establish a secure connection to transfer files and traverse the file system on both local and remote systems.
- Username + password: Client and server authentication via username and password.
- VPN: Security at the whole-of-server level for devices and/or users to connect to the platform (only available for private cloud customers).
Enterprise + proprietary security tools.
End-to-end encryption at all points.
Access our ultra-secure Rayven Private Cloud.
Fits your existing stack, policies + needs.
Every feature you need + others you’ll want tomorrow in one platform.
Easy-to-use, fast-to-deploy + delivering extreme capabilities; Rayven gives you an integration (iPaaS), ETL, Data, Workflow, Machine Learning, IoT, Analytics, AI + App Development platform in-one.
Pay only for what you do + get a platform that will grow with your business and needs - get started today, simply.
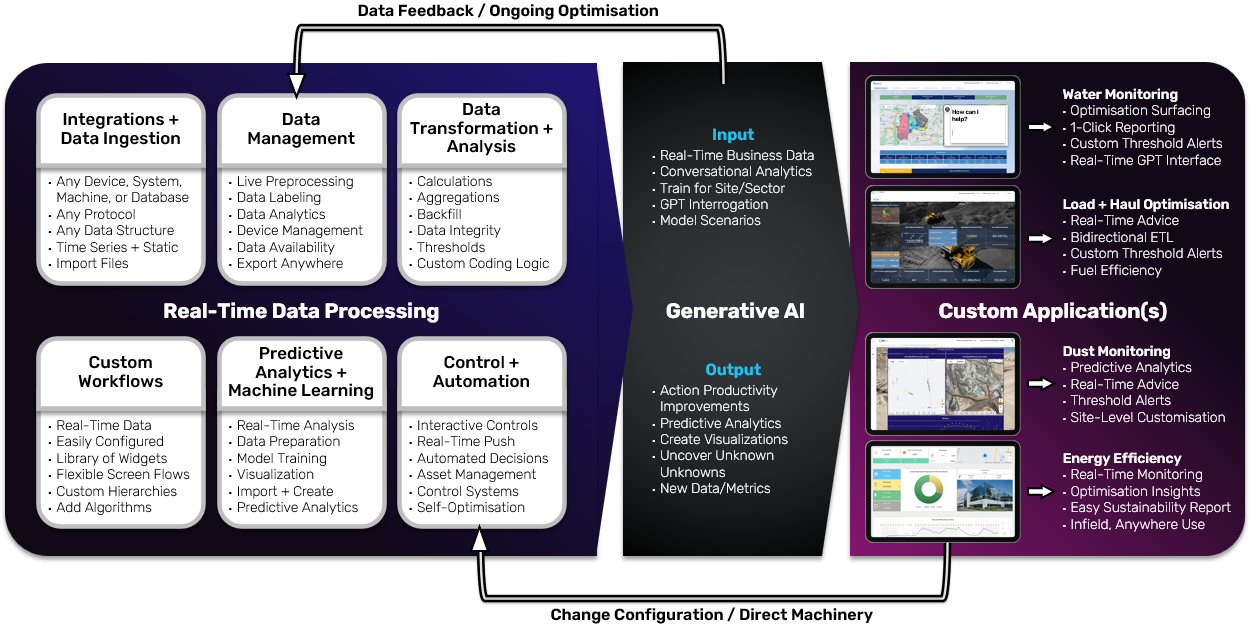
Explore some of our platform's other features:
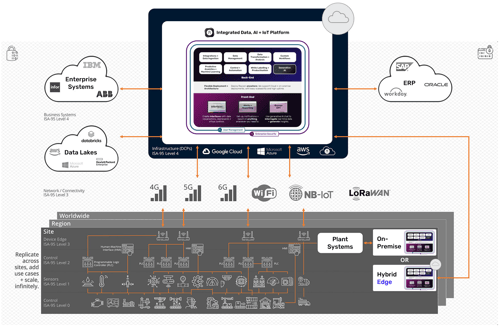
Deployment + Infrastructure.
Rayven complements your infrastructure, it doesn’t compete.
Rayven and the application built on it can be deployed on your existing infrastructure, in our private Cloud, or on-premise. With enterprise security built-in, our platform can be easily configured, deployed and maintained without an IT team’s involvement, putting you in total control.
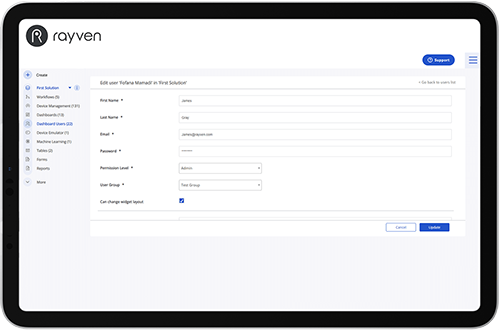
User Management.
Powerful industrial AI applications need to come with control, so our platform gives you all the tools you need. Manage passwords, access level + roles, create groups, and customise permissions.
Rayven's user management capabilities enable you to maintain security and integrity at all times.
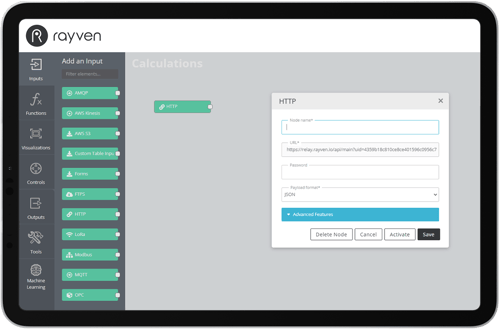
Integration + Data Ingestion.
Rayven is ultra-interoperable middleware that's can connect to any device, database, system, SaaS, machine, third-party data feed - anything - both fast and simply.
It does this using a unique toolkit of scripts, integration nodes and out-of-the-box connectors that can connect at a deeper, protocol level. The result is you can ingest data in any format, structure, static or time-series, via file import, and more.
Data Management.
Rayven makes it easy to manage data streams - no matter their origin + format - and store your data securely to ensure it's accessible, anywhere.
With real-time tagging, labelling + monitoring; our easy-to-use, enterprise-level tools make sure that your data is ready for anything both within and outside the platform.
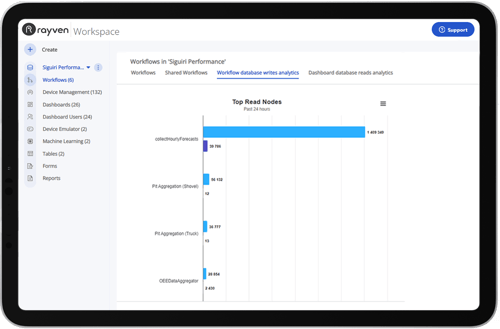
Control + Automation.
Our platform enables you to orchestrate processes and execute commands within and outside the platform.
Rayven enables you to create rules, control machines + put in place sophisticated automations that put in place self-optimising operations based on real-time, real-world performance - all without writing a line of code.



